Ever been bothered by a pesky adware from out of nowhere? Here’s a surefire way on how to remove adware from Google Chrome.
You’re browsing the web on your computer as always when suddenly there’s a pop-up ad that comes out from nowhere. You’re used to it, so you immediately click on the X button to close it out. Not a minute has passed and there’s a notification that says you’re about to install an extension.
What in the world is happening here?
Chances are, your computer is infected with adware that won’t stop until you get rid of it. These pesky bits of code will try to install other harmful adware, unwanted extensions and can even alter your browser’s settings. At worst, your computer will be infected with malware and virus attacks.Removing the adware from Google Chrome should be your first step. This ensures that your computer will be free of the security issues that come along with them.
Method 1: Removing Adware From Google Chrome Browser
Google Chrome is one of the most popular browsers out there because it supports add-ons and extensions, just like Mozilla Firefox. But not all extensions are equal. Some are malicious and seek only to infect your computer and steal private information from it.The adware could be silently running in the background or it could be wreaking havoc right in front of you. The best way of knowing whether you have a rogue extension is to search for it in your extensions list. Go through your Chrome extension settings, then uninstall any extension that you’re not familiar with.
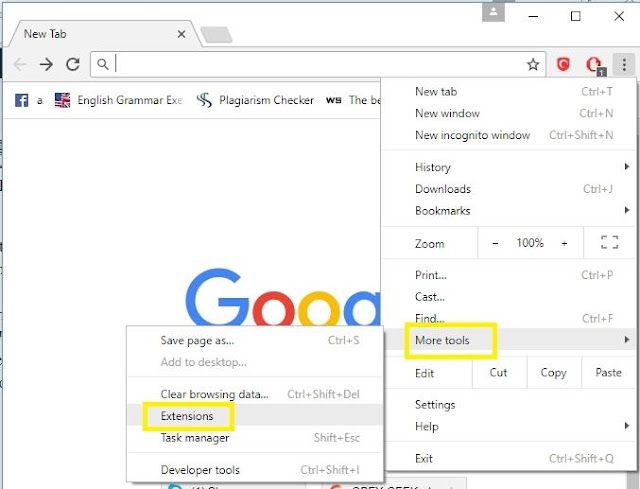
Step 1. Open your Google Chrome browser and hover your mouse over the menu. The icon is located at the top right corner and looks like three horizontal dots.
Step 2. A drop-down menu should appear. Scroll to the bottom and click on “More Tools”, then click on the option that says “Extensions”.
Step 3. A new tab comes up, and a list of your current Chrome extensions will be listed. You can use your mouse wheel to scroll through and identify the extensions you’re using and the ones that you’re not. If you’re unfamiliar with a particular extension, then chances are that it’s an adware masquerading as a real extension.
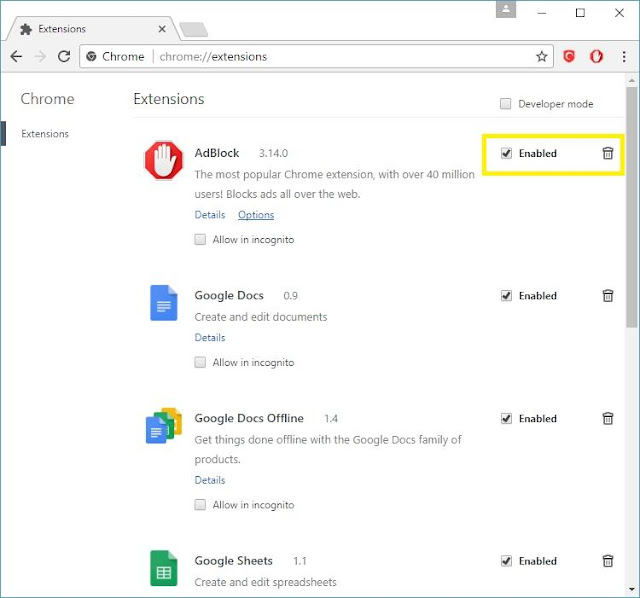
Step 4. Click on the trash icon located just right beside the extension to uninstall and remove it. If you’re unsure as to whether or not a particular extension is good or not, then you can temporarily disable it for the time being. Click on the box that has a check mark on it that says “enabled”. You’re done!
Method 2: Resetting Your Google Chrome Settings
Google has made its move against adware by alerting you when there’s a possible intrusion. But it’s not always effective because sometimes the adware slips past the browser’s defenses and change the settings without you knowing.The fix could prove to be very simple. It’s an out of the box solution- reset your Google Chrome settings so that the defenses will be active once again.
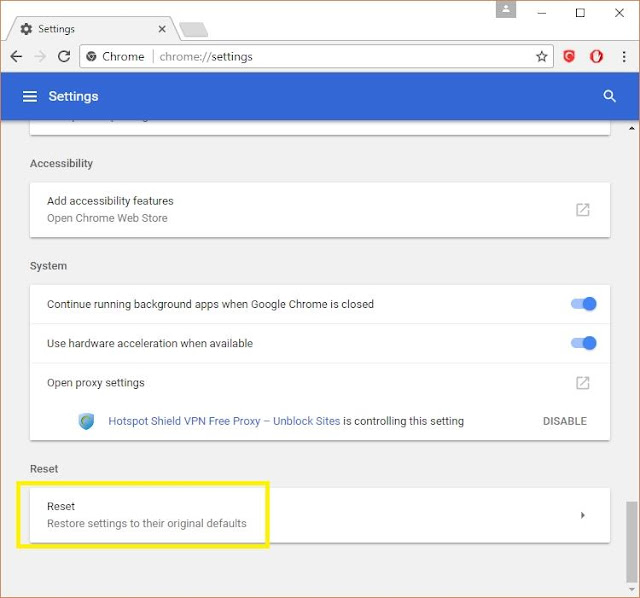
Step 1. Click on the three horizontal dots located at the top right part of your Chrome browser. Scroll down to the bottom and click on the Settings button.
Step 2. A new tab will come up. Click on the three horizontal lines located at the top left part of the page called Settings.
Step 3. Scroll down to the bottom part and look for the clock icon that says “Reset”. A confirmation dialog box will appear. Continue onwards and click the reset option to complete the process. You’re done!
Afterwards, you should be more careful about the software you’re installing and the extensions that you’re adding. If you have the time you can read through the End User License Agreement or check out a particular extension’s review before clicking on the “Install” button.
Prevention is always better than the cure. For this reason, you should install trusted security software – such as MalwareFox. It’ll ensure that your computer is safe from adware, malware, ransomware, and viruses and you’ll also get real-time protection when you mistakenly install suspicious adware. Not to mention you’ll increase your chances of fending off keyloggers, gray ware, Zero Day Attacks and ransomware.
Source - Tech Viral
Comments
Post a Comment